Security researchers have uncovered a significant vulnerability in WhatsApp that may have been actively exploited in the wild. Discovered internally by the WhatsApp Security Team, this flaw, identified as CVE-2025-55177, affects WhatsApp and WhatsApp Business on iOS, as well as WhatsApp for Mac.
The vulnerability has already been patched, but its potential use in targeted spyware campaigns signals a more troubling development: coordinated attacks chaining app-level and OS-level exploits to surveil specific individuals.
Read on for a breakdown of what CVE-2025-55177 is, how it was exploited, and what steps you can take to stay protected.
What Is CVE-2025-55177?
CVE-2025-55177 is a high-severity vulnerability (CVSS score: 8.0) rooted in insufficient authorization of linked device synchronization messages in WhatsApp.
This flaw could allow an attacker, without any legitimate association to the victim, to force the target device to process content from an arbitrary URL. In practical terms, this opens the door to Remote Code Execution (RCE) or content delivery from an attacker-controlled source, bypassing expected trust boundaries. Notably, this appears to be a zero-click exploit, meaning it can be triggered without any user interaction.
Affected versions include:
- WhatsApp for iOS prior to v2.25.21.73 (patched July 28, 2025)
- WhatsApp Business for iOS v2.25.21.78
- WhatsApp for Mac v2.25.21.78 (both patched August 4, 2025)
Meta has confirmed that this flaw was likely exploited alongside an Apple vulnerability (CVE-2025-43300), raising the severity of the situation.
CVE-2025-43300: Apple ImageIO Vulnerability Amplifies Attack Chain
The official advisory points to the chaining of CVE-2025-55177 with CVE-2025-43300 (CVSS: 8.8), an Apple platform vulnerability affecting iOS, iPadOS, and macOS. This OS-level bug involves an out-of-bounds write in the ImageIO framework, which could lead to memory corruption during image processing.
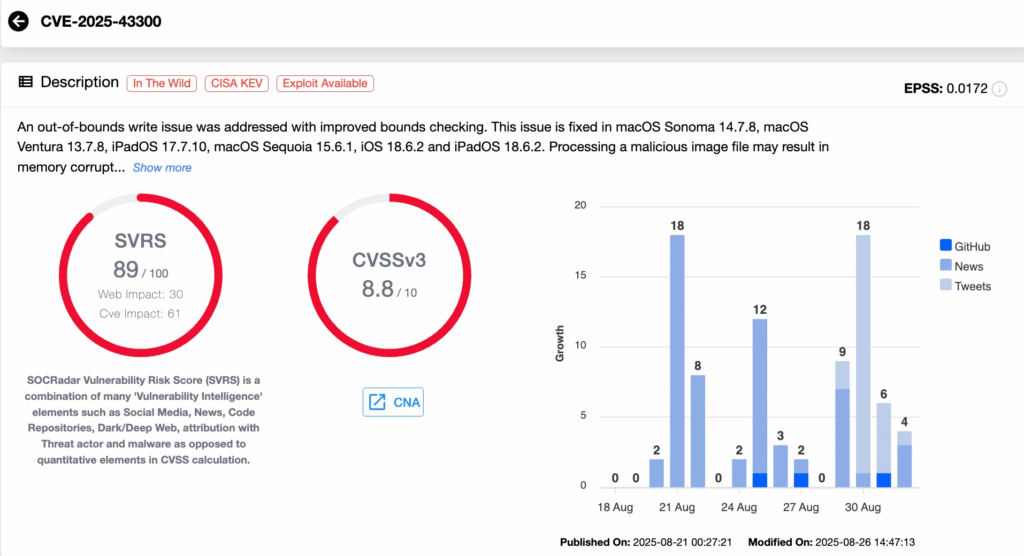
Details of CVE-2025-43300 (SOCRadar Vulnerability Intelligence)
How CVE-2025-55177 Was Used in Targeted Attacks
The combination of the two flaws potentially enabled a highly stealthy spyware deployment pipeline. Because the exploit is zero-click, the victim does not need to open a file, click a link, or take any action at all. That level of automation drastically reduces detection risk, allowing spyware to be implanted silently and rapidly.
While the origin of the campaign and the spyware vendor remains undisclosed, the nature of the attack implies an advanced and well-resourced adversary.
This isn’t just a case of app-level misconfiguration. It reflects the growing trend of multi-layered exploits, where app and OS bugs are woven together to bypass user defenses and implant spyware with minimal visibility.
Mitigation Steps to Secure WhatsApp & Apple Devices
Users who may have been affected received a direct alert from WhatsApp, along with strong recommendations to secure their devices. Even if you weren’t notified, it’s critical to take the following actions:
- Update immediately: Make sure you’re running the latest version of WhatsApp on all platforms.
- Apply OS patches: Install the latest iOS/macOS/iPadOS updates from Apple, particularly those addressing CVE-2025-43300.
- Review connected devices: Remove any unfamiliar or unused linked devices from WhatsApp’s multi-device settings.
- Factory reset: If you suspect compromise, perform a full device factory reset to clear any lingering spyware.
This incident highlights the growing risk of zero-click exploits, reinforcing the importance of keeping apps and operating systems up to date to stay protected.

