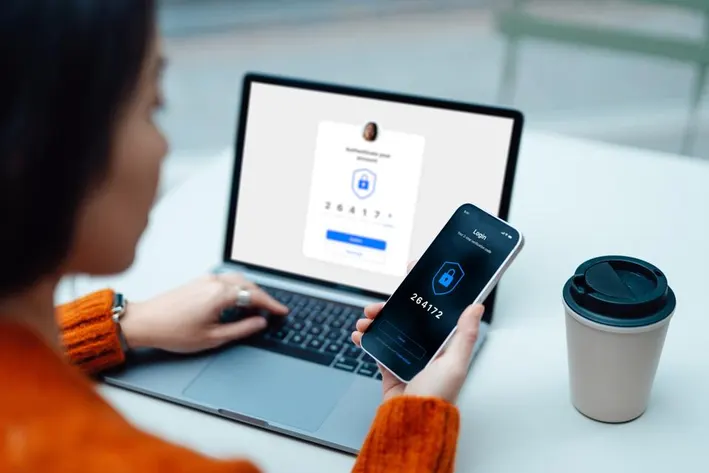
In an era where data breaches make headlines almost daily, securing your online accounts goes beyond just a strong password. Enter Multi-Factor Authentication (MFA)—a simple yet powerful layer of protection that's becoming essential for everyone from casual social media users to corporate executives. If you've ever received a code on your phone after entering your password, you've experienced MFA in action. This post dives into what MFA is, how it works, its benefits, and tips for implementing it effectively. Whether you're new to cybersecurity or looking to level up your defenses, understanding MFA can significantly reduce your risk of unauthorized access.
Breaking Down MFA: The Basics
Multi-Factor Authentication, also known as two-factor authentication (2FA) or multi-step verification, requires users to provide two or more proofs of identity before granting access to an account or system. It's like having multiple locks on your door—instead of just a key (your password), you need a fingerprint or a code too.
The "factors" typically fall into three categories:
- Something You Know: This is your password or PIN.
- Something You Have: A physical device, like your smartphone for receiving a one-time code, or a hardware key (e.g., YubiKey).
- Something You Are: Biometrics, such as a fingerprint, facial recognition, or voice pattern.
Most MFA setups combine the first two for simplicity, but advanced systems might incorporate all three. When you log in, after entering your password, the system prompts for the second factor—ensuring that even if a hacker steals your credentials, they can't get in without that extra piece.
How MFA Works in Practice
Imagine logging into your email: You type your password (factor one), then receive a text with a six-digit code (factor two) that you enter to proceed. Behind the scenes, services like Google or Microsoft use secure protocols to generate and verify these codes, often time-limited to prevent reuse.
Common MFA methods include:
- App-Based Codes: Apps like Google Authenticator or Authy generate codes offline, avoiding SMS vulnerabilities.
- Push Notifications: Apps send alerts to your device for one-tap approval.
- Hardware Tokens: Physical devices that plug in or connect via NFC for high-security needs.
- Biometric MFA: Integrated with devices like smartphones for seamless, passwordless logins.
While convenient, MFA isn't foolproof—attacks like SIM swapping (where hackers hijack your phone number) can bypass SMS-based methods. That's why experts recommend app-based or hardware options for better security.
The Benefits: Why Bother with MFA?
The primary perk? It dramatically reduces breach risks. Studies show MFA blocks over 99% of automated attacks, like credential stuffing where hackers try stolen passwords en masse. If your password leaks in a data breach (which happens to millions annually), MFA acts as a safety net.
Other advantages:
- Enhanced Privacy: Protects sensitive data in banking, healthcare, or work accounts.
- Compliance and Peace of Mind: Many regulations (e.g., GDPR, HIPAA) mandate MFA for certain sectors, and it gives users confidence in an insecure online world.
- Cost-Effective: Most MFA solutions are free or low-cost, built into platforms like email providers or social networks.
Without MFA, you're relying solely on passwords—which are often weak, reused, or easily guessed. Cybercriminals thrive on this, using tools to crack them in seconds.
Potential Drawbacks and How to Overcome Them
MFA isn't without challenges. It can add friction to logins, potentially frustrating users. If you lose your phone, recovery might involve backup codes or alternate methods—always set these up in advance.
To make MFA smoother:
- Choose user-friendly options like push notifications over codes.
- Use a password manager that integrates MFA for streamlined access.
- Educate yourself on recovery processes to avoid lockouts.
For organizations, implementing MFA company-wide through tools like Okta or Azure AD ensures consistency while minimizing user resistance.
Getting Started: Enable MFA Today
Ready to amp up your security? Start here:
- Audit Your Accounts: Check major services (Google, Apple, Microsoft, social media) in their security settings to turn on MFA.
- Opt for Secure Methods: Prefer authenticator apps over SMS for resilience against phone-based attacks.
- Backup Your Setup: Save recovery codes in a secure spot, like a password manager or encrypted file.
- Spread the Word: Encourage friends, family, or colleagues to adopt MFA—collective security strengthens everyone.
In summary, MFA is a straightforward upgrade that punches above its weight in cybersecurity. Don't wait for a breach to motivate you; enable it now and sleep easier knowing your digital life has an extra guard at the gate.