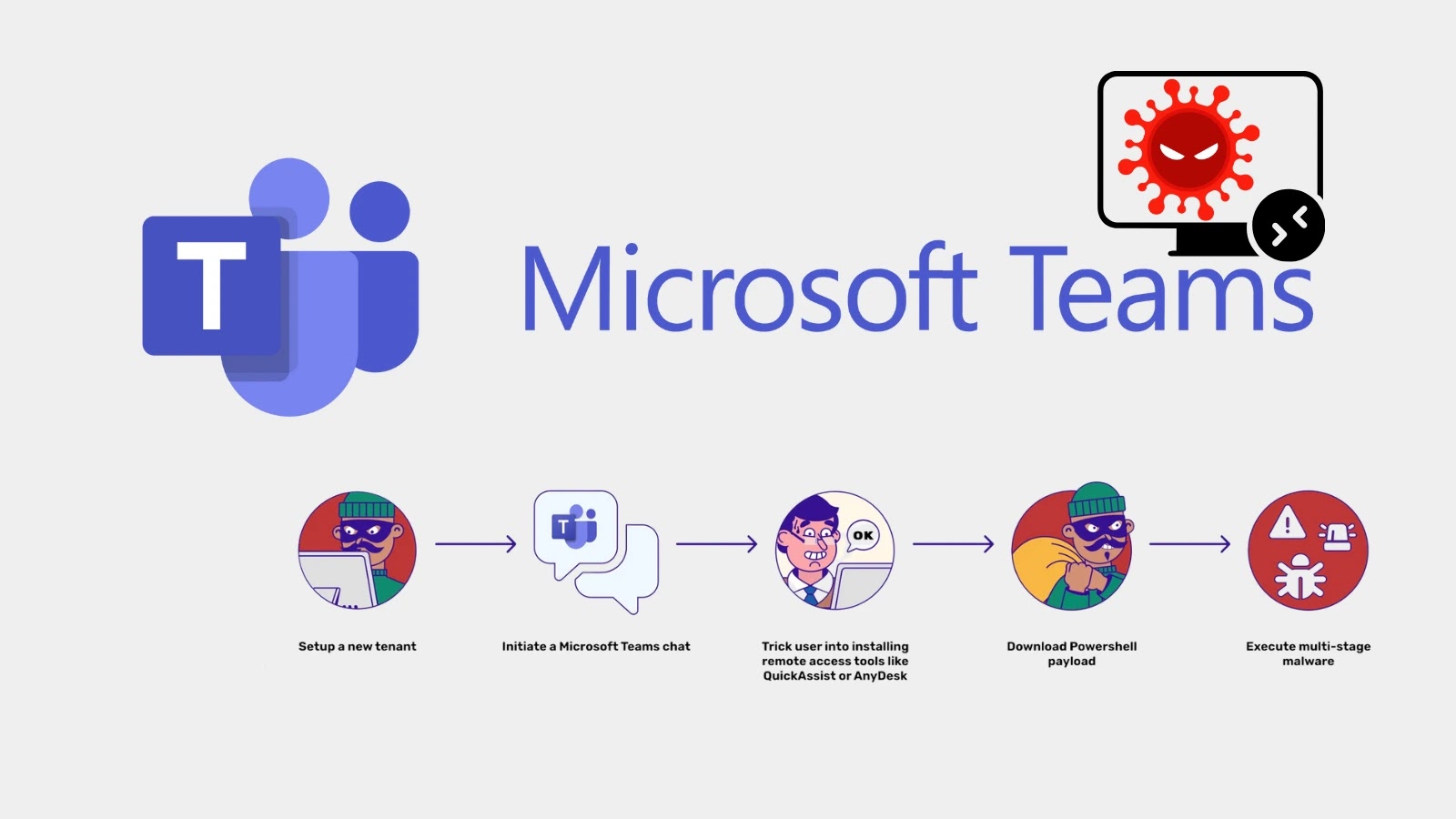
Cybercriminals are increasingly weaponizing Microsoft Teams, exploiting the platform’s trusted role in corporate communications to deploy malware and seize control of victim systems.
In a sophisticated campaign, threat actors are impersonating IT support staff in Microsoft Teams chats to trick employees into granting remote access, marking a dangerous evolution from traditional email-based phishing attacks.
Social engineering remains a highly effective tactic for hackers, and as businesses have integrated platforms like Microsoft Teams into their core operations, attackers have followed. The inherent trust employees place in internal messaging makes it a fertile ground for deception.
Recent campaigns analyzed by Permiso cybersecurity researchers reveal a multi-stage attack that begins with a simple message and culminates in the deployment of potent, multifunctional malware.
PowerShell-based Malware via Microsoft Teams

Attackers often use checkmark emojis to simulate a verified status and leverage Microsoft’s "onmicrosoft.com" domain structure to appear as if they are part of the organization.
Posing as IT staff addressing a routine issue like system maintenance, the attackers build rapport with their target.
Once trust is established, they persuade the employee to install remote access software, such as QuickAssist or AnyDesk, under the guise of providing technical assistance. This critical step gives the attacker a direct foothold into the user’s machine and the corporate network.
While similar techniques involving remote access tools have been linked to ransomware groups like BlackBasta since mid-2024, these newer campaigns are more direct, often forgoing the preliminary mass email campaigns seen in the past.
The malicious payloads have also diversified, with recent incidents involving the DarkGate and Matanbuchus malware loaders.
Once remote access is secured, the attacker executes a PowerShell command to download the primary malicious payload. This script is far from simple, equipped with capabilities for credential theft, establishing long-term persistence, and remote code execution, Permiso said.
To evade detection and complicate removal, the malware can designate its own process as “critical,” which would cause the system to crash if terminated.
It also uses a legitimate-looking Windows credential prompt to trick users into entering their passwords, which are then exfiltrated to an attacker-controlled server.
Analysis of the payload’s code revealed hardcoded encryption keys that link the campaign to a known financially motivated threat actor tracked as Water Gamayun (also known as EncryptHub).
This group has a history of combining sophisticated social engineering with custom malware to target English-speaking IT professionals and developers.
Employees must be trained to remain vigilant against unsolicited contact, even on trusted internal platforms. All requests for credentials or the installation of remote access software should be independently verified through a known, separate communication channel.
As threat actors continue to innovate, a defense-in-depth strategy, combining technical controls with robust user education, is essential to protect against attacks that turn collaboration tools into conduits for compromise.